- Digital Kleptos
- Posts
- How Safe Is Public Wi-Fi? What’s a “normie” to think?
How Safe Is Public Wi-Fi? What’s a “normie” to think?
A guy in Australia is now sitting in jail for tricking people into using fraudulent airport Wi-Fi.
Happy Tuesday! For years we’ve heard that using public Wi-Fi can be a scary problem. More recently, cybersecurity experts have explained that although this was definitely a problem 10 years ago, because of improvements to the structure of the Internet, it’s no longer a real concern. |  |
Let’s imagine a couple of savvy business travelers, Bob and Alice. They’re leaving on a trip next week, the issue of public Wi-Fi came up, and now they’re searching online for an answer. What will they find?
— Anthony Collette
Founder, Loistava Information Security
Is Using Public Wi-Fi Risky?
That’s a reasonable question for any traveler to ask. During the past 10 years, we’ve all seen many warnings issued by experts, government offices and law enforcement agencies. It sounds like a real problem.
However, many cybersecurity experts now believe that this problem is vanishingly rare and unlikely to affect normal people. They point to the many improvements in the structure of the Internet, including updates to modern browsers. They consider the warnings about public Wi-Fi to be “persistent myths.” And they might be right.
What’s Up With Bob And Alice?
Let’s check back in with our intrepid travelers Bob and Alice, who are now curious about the current state of affairs regarding the safety (or possible lack thereof) of public Wi-Fi. This question only came up because they’re traveling through airports, and it’s now top of mind. Let’s assume they fire up Google and start searching for “airports Wi-Fi hacking”. What messages will Bob and Alice be exposed to?
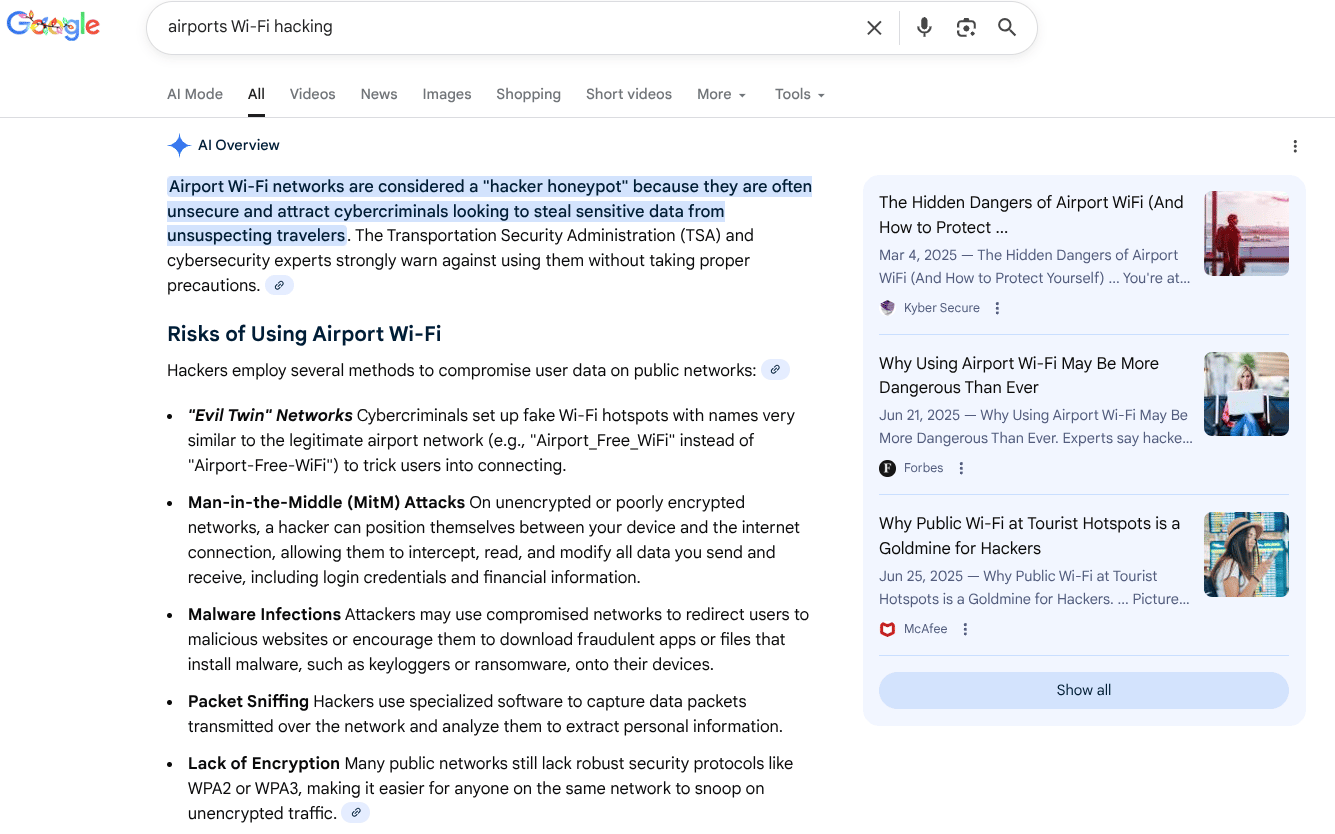
Well, that’s certainly not subtle.
The AI Overview begins: “Airport Wi-Fi networks are considered a "hacker honeypot" because they are often unsecure and attract cybercriminals looking to steal sensitive data from unsuspecting travelers. The Transportation Security Administration (TSA) and cybersecurity experts strongly warn against using them without taking proper precautions.”
The Overview continues with gnarly descriptions of various ways Digital Kleptos™ in airports can cause havoc. Hmmm . . . that’s certainly enough to raise at least one Spock eyebrow.

Since Bob and Alice are business folks, they notice a link to a Forbes story, click on it, and are greeted with this headline: Why Using Airport Wi-Fi May Be More Dangerous Than Ever. The story begins with a security consultant and her client attempting to log in to public Wi-Fi at JFK International Airport. When logging in, the public Wi-Fi asked for her birthdate. This was a persuasive red flag and convinced the security consultant that the Wi-Fi wasn’t safe. "Real airport networks never do that," she said.
Assuming Bob and Alice read on a bit further, they notice something about a guy in Australia who got arrested for Wi-Fi shenanigans at multiple airports there. Airport employees got wise to a guy acting odd, alerted the police, and eventually law enforcement determined that the guy had set up fake Wi-Fi at three different airports, on flights, and at various locations related to his employer. The fake Wi-Fi served up look-alike login pages and prompted unsuspecting travelers to log in using an email or social media account. Dozens of login credentials were then saved on the hacker’s equipment. The guy then illegally accessed social media and other accounts linked to women to monitor communication and steal private and intimate images and videos. That’s probably even worse than having money drained from a bank account. He’s now sitting in jail for at least 5 years.
The very first search result after the AI Overview is a link to this CNBC story: Why it’s time to take warnings about using public Wi-Fi, in places like airports, seriously. The article mentions that airports generally outsource public Wi-Fi and aren’t responsible for maintenance or security. Airline and airport personnel (two very different workforces) aren’t equipped, prepared or trained to handle or mediate hacking accusations. Interviewed experts are quoted saying that these kinds of attacks are “definitely” occurring with regularity in the United States, it’s just rare for someone to get caught. The equipment hackers use to do this doesn’t look out of place and some of it is quite compact. This odd combination of dynamics makes airports an especially juicy target.
So far we’ve only explored the AI Overview, the first search result, a Forbes story and a link or two about Australia. Let’s assume our travelers’ rabbit hole ends here.
What are Bob and Alice likely to think?
At this point it’s perfectly reasonable for reasonable people to conclude that there’s a real problem, especially in airports, because of a combination of unusual dynamics.
Can we blame them?
Cybersecurity is fascinating, and I have tremendous respect for cybersecurity practitioners. However, in this particular case, I don’t envy you. Overcoming the messaging that most internet users are exposed to — without going much further than the top half of the first page of search results — is a herculean task.
Cybersecurity practitioners are not alone in explaining risk to the public.
There’s a comparable dynamic in medicine. An entire consulting specialty exists to help doctors find the answer to a seemingly straightforward question: “How should I talk to my patients?” The mass media has always covered medical news, so patients have always asked their physicians about the messaging they encounter. The Internet has supercharged that dynamic. An MD can pretend that messaging doesn’t exist. Or they can choose to accept that messaging as one data point, one piece of reality, and find a way to deal with it as they explain options and risk to their patients.
Like medicine, law and many other professions, cybersecurity is an advice-giving vocation. The perception of credibility in the mind of the patient (or client) is truly important. If you give cybersecurity advice to someone, and they don’t respond the way you’d prefer, the reason may be simple: someone else got to them first.
Perhaps it was a conversation, or an article they read, or a YouTube video.
If you tell people there is no problem here, but they quickly and easily find a clear and compelling description of the problem, what are they likely to think? How does that affect their perception of your credibility? How best to manage that?
What about the rest of us?
It’s helpful to note that none of the sources of these media stories is trying to sell anything; these aren’t vendors spreading fear, uncertainty and doubt. We can benefit from becoming aware of these recent events, and staying up-to-date as conditions change.
It’s clear there are real concerns about using public Wi-Fi, particularly in airports. What can you do about it? Consider using your own cellphone hotspot instead of an uncertain network. Both Apple and Google provide built-in VPN services that are free and easy to use, so that’s always available. If you must use airport Wi-Fi, avoid logging in with any personal details — such as an email or social media account. And give serious thought to avoiding online banking transactions before your flight or during a layover. Overall, one of the most effective solutions (at the airport or elsewhere) is to set up Multi-factor Authentication (MFA), choosing one of the “better” or “best” scenarios.
Bob and Alice have effective options, and so do we!
UPDATE: A recent report by Dan Goodin, Senior Security Editor for Ars Technica, detailed a newly verified problem with Wi-Fi, dubbed AirSnitch. The article is quite technical as it describes a problem with networking and the isolation techniques used to create guest Wi-Fi access. “For now, client isolation is similarly defeated — almost completely and overnight — with no immediate remedy available.” Dan mentions that some of the problem can be lessened by using a VPN, but that VPNs in this scenario shouldn’t be regarded as much more than a bandage. Dan suggests one possibility is “For many people, that may mean steering clear of public Wi-Fi networks altogether.”
Join us
Weekly resources to help keep you safer online — protecting you from hackers, online scammers, and other Digital Kleptomaniacs™.
No spam. No selling your email. Just factual, actionable information once a week, from people who truly care about online security. You can unsubscribe any time — but we hope you’ll want to stay with us on this journey.
Cybersecurity is a modern form of wealth, and you deserve to keep what you've earned.
Looking forward to connecting again next week.
— Anthony Collette
Reply